Gone are the days when you would send an email and not have to worry about it getting delivered. SPAM has been around for almost as long as email, and receivers today have quite a job deciding what is real and what’s not. Wouldn’t it be great if legitimate senders had a clever way of helping them accomplish this? If there was only something we could do to help our email hit the Inbox and separate us from the junk. Well, keep reading because that’s exactly what Email Authentication is all about. We’ll show you how to do it in this article.
Why this is important
Authentication prevents spammers from using your domain to send emails without your permission. There are 3 main protocols in use today (SPF, DKIM, and DMARC) and each helps validate your email is legitimate in an effort to help maximize your delivery.
What is SPF?
Sender Policy Framework (SPF) is an authentication standard that has been around since 2003 and works by publishing a list of IP addresses that are allowed to send on your domain’s behalf. Receiving mail servers will use SPF to verify that messages sent from your domain were sent by one of these IP addresses. SPF authenticates the Return-Path: domain with the IP address used to send the email.
SPF helps protect your domain against spoofing and helps prevent your outgoing messages from being marked as spam by receiving servers. Whether the SPF passes (or fails) can be seen in the Authentication-Results: header. However, this only validates the server sending the email; it does not ensure that the content has not been tampered with. For that, we need DKIM (Domain Keys Identified Mail).
What is DKIM?
DKIM stands for DomainKeys Identified Mail and is a complex method of authentication that encrypts the email in transit by signing it with a digital signature which creates a unique string of characters called a “hash value.” When a receiver detects an email has been signed using DKIM, it will authenticate the message using a pair of “keys” :
1st key – “Private Key” is kept safe by the sender and cannot be shared.
2nd key – “Public Key” is stored in the DNS of the client’s From domain.
When the email is received, the receiver will use these keys to decrypt the hash value in the
header and if both keys match, it shows the email has not been altered and the DKIM signature is then verified. If the keys do not match, the DKIM signature will fail and the recipient’s ISP will be more likely to place the email in the Spam box or block it outright. But how can I see who is using my domain without my permission? Enter DMARC.
What is DMARC?
DMARC stands for Domain-based Message Authentication, Reporting & Conformance, and it’s a standard that mail servers use to determine if an incoming email is coming from sources that the domain sending the email trusts.
DMARC uses SPF or DKIM to verify if the sender is genuine, and takes authentication one step further by sending a report of who is using their domain back to the sender. For DMARC to pass, the email must pass either SPF or DKIM, and the domain in the From header must be aligned with the corresponding SPF or DKIM domain.
The main advantage of DMARC is that it’s the sender who controls what happens to spam sent using their domain, not the receiver. So you can tell the receiver to block mail you didn’t send, and better yet, you get a report of mail that is using your domain without your permission – so DMARC is very powerful and is the gold standard in use today.
Click for a quick overview on how SPF works by DMARCIAN.
Click for a quick overview on how DKIM works by DMARCIAN.
Click for a quick overview of how DMARC works by DMARCIAN.
How to authenticate your domain DNS
To do this, you will need to access the DNS records for your domain with its hosting provider and add the correct DNS settings. You can follow this guide:
- 1. Visit your domain provider’s site and log in.
- To find out where your domain is managed, contact the person or team that manages your website or email address.
- If you’re not sure where to find this information, we’ve compiled the four biggest domain hosting service providers for your reference:
* GoDaddy
* Network Solutions
* Domain.com
* namecheap.com - You can also look up your domain host by checking this website: https://lookup.icann.org/.
- 2. On the top right part of the platform, click on the arrow next to your username.
- 3. Select Account.
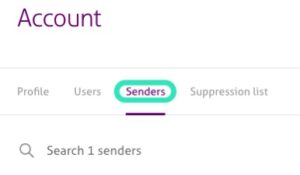
- 4. In the Account page, select the Senders tab.
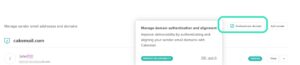
- 5. In the menu to manage the sender email addresses and domains, select the option Authenticate domain.
- 6. Follow the steps outlined in this page to add the platform’s records to your DNS.
- 7. Wait for the verification.
- 8. The Domain authentication status is displayed on the last step.
Authenticating with DMARC
DMARC:
Please make sure you have already set up the SPF/DKIM on your From domain before proceeding with DMARC.
Once your SPF/DKIM is done, we recommend you set up an account with DMARCIAN and run through their DMARC RECORD WIZARD to create your DMARC record.
Why DMARCIAN?
DMARCIAN is a trusted partner with our application and as soon as you set up your DMARC record, you will start to get flooded with XML reports telling you who is using your domain. These reports provide insight into how your email is moving through the ecosystem and allow you to identify if anyone else is using your domain. Making sense of these reports can be tricky and they can be numerous. Not only can DMARCIAN help create your DMARC record with ease, but their platform can also be used to view these XML reports and provide visualization on how your email domains are being used so you can take action. You will need this visibility in order to ensure you do not block legitimate mail before moving your DMARC policy towards p=quarantine or p=reject.
Who will send me these reports?
What started with a small list of ISPs like AOL, Yahoo, and Gmail has grown into a long list around the world with more and more being added every day. Here is a current list of known receivers checking for DMARC:
Amazon WorkMail, AOL, Apple, ATT, BT Mail, Cisco Email Security, Comcast, Gmail, Google Apps, Hotmail, Hover, LaPoste, Libero.it, Mail.ru, Mimecast, Office 365, Onet, Proofpoint, Rackspace, Rogers, SFR, Shaw, Skynet Proximus, Sophos, SpamExperts, Symantec, Vade Secure, Yahoo! ,Yahoo! UK, Ziggo, Zoho.
The time to set up DMARC and secure your domain is now!